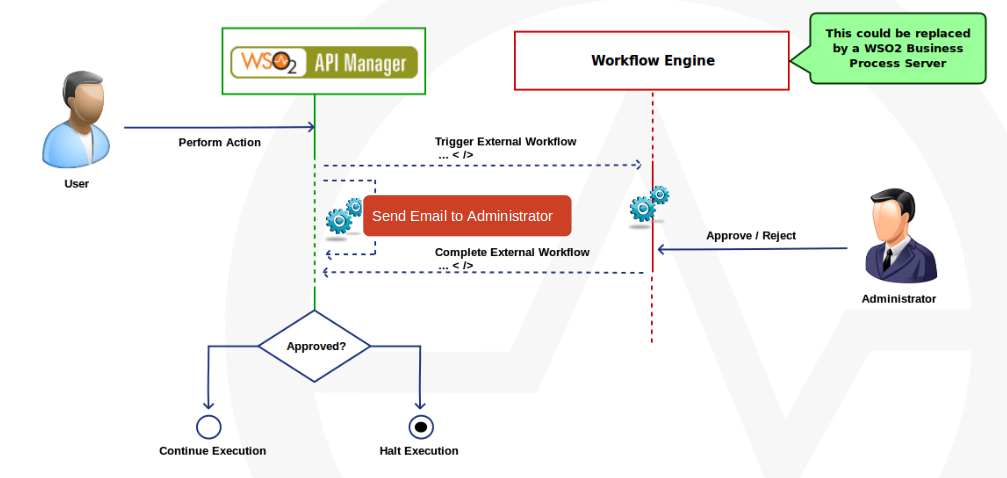
Troubleshooting Swagger issues in WSO2 API Manager
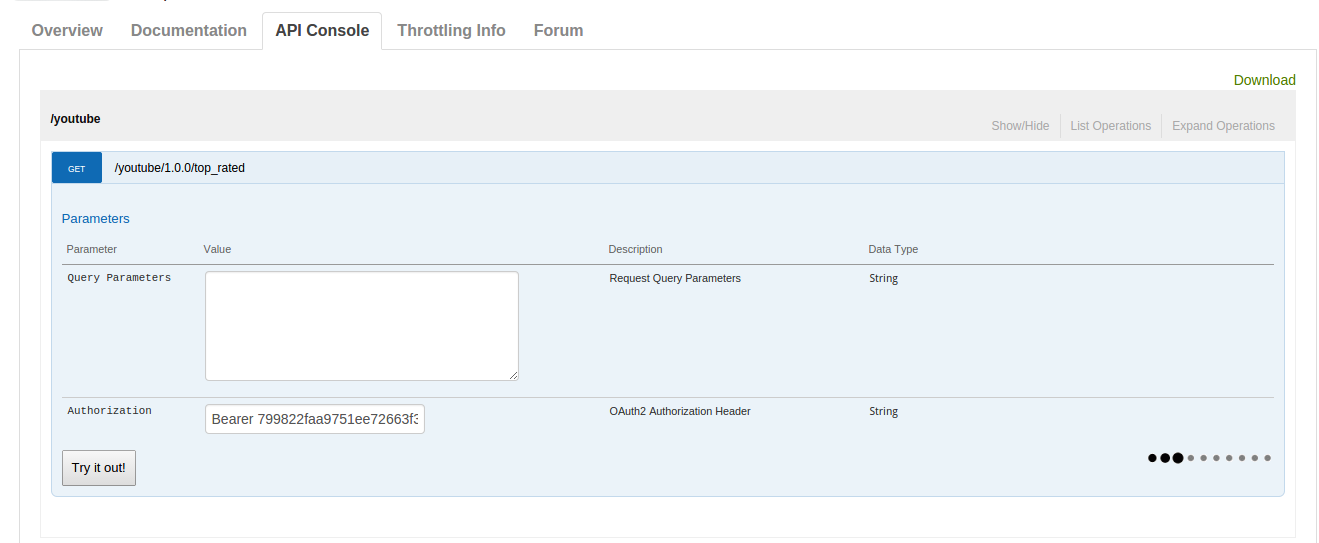
WSO2 API Manager provides this functionality through the integration of Swagger ( https://developers.helloreverb.com/swagger ). Swagger-based interactive documentation allows you to try out APIs from the documentation itself which is available as the "API Console" in API Store. There are certain requirements that need to be satisfied in order to swagger Try-it functionality to work. First requirement is to enable CORS in API Mananger Store. This documentation describes how that should be done. But most of them face many issues in getting the swagger Try-it into work. So this blog post describes common issues faced by users with Swagger and how to troubleshoot them. Issue-1 API Console keeps on loading the response for ever as below. Cause -1 API resource not supporting OPTIONS HTTP verb. Solution Add OPTIONS HTTP verb for API resources as below. Then Save the API and Try again. Cause -2 Backend endpoint not supporting